Automation and intelligent systems are now foundational across industries—consumer electronics, automotive,
healthcare, robotics, and industrial control. At the heart of many of these products sits the operating system.
Among available options, Embedded Linux stands out for its balance of flexibility, stability,
licensing freedom, and long-term viability. Recent market analyses project the embedded Linux ecosystem to continue
expanding through 2025 and beyond, driven by IoT adoption, connected machinery, and edge AI.
This guide distills how to evaluate, select, and deploy an embedded Linux distribution that fits your hardware,
security posture, and product roadmap. It covers common distribution families, decision criteria, development
challenges, and a practical comparison to help you ship faster—with fewer surprises in production.
1) Market Context & Why Embedded Linux
Embedded Linux has matured into a reliable, production-grade foundation for smart devices and industrial systems.
Vendors embrace it because:
- Hardware breadth: Broad support for ARM, x86, RISC-V, and diverse SoCs/SOMs.
- Customizability: Kernel, toolchain, and root filesystem can be tailored to footprint and performance targets.
- Ecosystem and longevity: A massive developer community, upstream drivers, and long-term maintenance branches (e.g., LTS kernels).
- Total cost of ownership: License flexibility and reuse of platform components across product lines.
In practice, Embedded Linux powers HMI panels, gateways, industrial controllers, surgical devices, ADAS data loggers,
mobile robots, and high-brightness outdoor kiosks—anywhere that needs deterministic control plus rich connectivity.
2) Distribution Types & Typical Use Cases
Full-featured general-purpose bases
Distributions such as Debian and Ubuntu Core offer large package repositories,
convenient package managers (APT/Snap), and faster prototyping—great for devices that need
a desktop-class userspace, rich networking stacks, or complex GUIs.
- Pros: Fast development, abundant docs, easy access to libraries and middleware.
- Cons: Larger footprint, more background services, and occasionally slower boot.
- Typical fit: Prototyping, edge analytics nodes, maintenance tools, evaluation boards.
Build-your-own frameworks
Yocto Project (with Poky, BSP layers) and Buildroot let you assemble a minimal,
reproducible distribution optimized for your SoC and storage limits. They’re the default choice for
long-lived industrial products where footprint, bill of materials, and update control matter.
- Pros: Small images, precise dependency control, reproducible builds, long-term maintainability.
- Cons: Steeper learning curve; you’ll own more of the build/debug pipeline.
- Typical fit: Mass-produced devices, HMIs, gateways, safety-adjacent controllers.
Vendor or silicon-specific SDKs
Many silicon vendors ship BSPs, pre-integrated kernels, and sample images. These accelerate bring-up but may lag
upstream or require vendor-specific workflows.
- Pros: Fastest hardware enablement; demo images get you to “first boot” quickly.
- Cons: Patch downstream kernels, heterogeneous tooling, variable documentation quality.
- Typical fit: Early evaluation, proof-of-concept, or where vendor support is contractually required.
3) Key Selection Criteria
- Hardware alignment: Verified support for your SoC/SOM, GPU, camera, display, and fieldbus (CAN, Modbus, EtherCAT).
Confirm kernel version, device tree, and driver maturity. - Footprint & performance targets: Define boot time, memory budget, storage type (eMMC/NAND/NOR), CPU/GPU utilization,
and display refresh requirements early. - Security & update model: Choose an OTA strategy (A/B slots, RAUC, Mender, SWUpdate), signing, secure boot/TPM,
and CVE patch cadence. - Ecosystem & longevity: Favor active communities, LTS kernels, long-term branches, and clear BSP maintenance policies.
- Tooling & developer experience: Reproducible builds (BitBake, Buildroot, containers), CI integration,
remote debugging, and trace tooling (perf, LTTng, eBPF). - Licensing clarity: Understand GPL/LGPL/MIT usage and obligations for shipping products and distributing toolchains.
4) Common Development Challenges (and how to avoid them)
Hardware variance & driver gaps
Even small SoC revisions can change clocks, pinmux, or display timings. Keep your device tree in source control,
upstream patches where possible, and align your kernel with a vendor or community LTS to simplify patch flow.
Resource constraints
Embedded devices rarely tolerate bloat. Strip services, compile with size-oriented flags, and
prefer static assets where appropriate. Profile early with top, perf, and
systemd-analyze to catch memory leaks or slow boot units.
Display pipelines & HMI responsiveness
For Embedded HMIs, verify DRM/KMS, touch controllers, and backlight drivers. Measure input latency and frame pacing; use
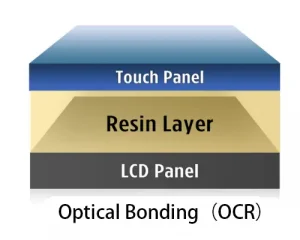
double buffering and GPU composition where supported. Consider high-brightness panels or optical bonding for outdoor use.
OTA robustness & field reliability
Updates must survive power loss and network issues. Use atomic image updates (dual slots),
integrity checks, and rollback policies. Log every transition and test update failure modes on real hardware.
5) Standards, Security & Compliance
- POSIX and toolchain parity: Improves portability across architectures.
- Hardening: ASLR, RELRO, stack canaries, seccomp, namespaces, AppArmor/SELinux.
- Cryptography & secure boot: U-Boot verified boot, FIT images, TPM/TEE integration, encrypted storage.
- Sector-specific requirements: e.g., ISO 26262 (automotive), IEC 62304 (medical software),
IEC 62443 (industrial cybersecurity). Choose a base that simplifies audits and traceability.
6) Popular Options Compared
| Option | Strengths | Watch-outs | Best for |
|---|---|---|---|
| Yocto Project | Reproducible, highly customizable, layered BSP model, long-term maintainability. | Learning curve, longer initial bring-up. | Production devices with strict footprint, security, and longevity constraints. |
| Buildroot | Fast, simple, minimal images; great for small systems and CI pipelines. | Fewer “distro-like” conveniences; updates often image-based. | Small headless systems, appliances, and single-purpose gateways. |
| Debian (armhf/arm64) | Huge repo, familiar tooling, rapid prototyping, stable releases. | Larger images, background services; must harden aggressively for production. | Prototypes, edge analytics nodes, tools, internal utilities. |
| Ubuntu Core | Transactional snaps, confinement, easy app delivery. | Snap model may not fit all products; image size/boot time considerations. | Modular devices needing app store-style delivery and isolation. |
| Vendor BSPs/SDKs | Fastest hardware enablement, tuned demos for codecs/ISP/GPU. | Downstream patches; update cadence depends on vendor. | Evaluation, PoC, or where vendor support is mandatory. |
7) A Practical Evaluation Workflow
- Define non-negotiables: boot time, RAM/flash limits, display timing, security posture, OTA strategy.
- Shortlist candidates: pick 2–3 distributions that demonstrably support your SoC and peripherals.
- Bring-up on target hardware: verify device tree, GPU/DRM, touch, fieldbuses, camera, storage, Wi-Fi/BLE.
- Measure early: boot charts, CPU/GPU load, memory footprint, UI latency, network stability, update rollback.
- Harden and document: disable unused services, apply kernel hardening, configure firewalls,
log decisions (kernel, DT, patches) for audits and future maintainers. - Automate builds and updates: containerize build environments, add CI for images, sign artifacts,
and test OTA in hardware-in-the-loop rigs.
8) FAQ
Is Yocto overkill for small projects?
Not necessarily. If you need a minimal, reproducible image with tight control of dependencies and security,
Yocto pays off—even for modest devices. For ultra-fast experiments, Debian/Ubuntu can still be useful early on.
How do I keep images secure in the field?
Use verified boot (U-Boot + signed FIT), encrypt sensitive partitions, apply kernel/userspace hardening,
and ship atomic OTA with rollback. Track CVEs and schedule patch windows.
What about real-time?
Consider PREEMPT_RT kernels, isolate time-critical threads (CPU shielding), and avoid UI contention on the same cores.
Some industrial SoCs provide auxiliary cores (MCUs) for hard real-time tasks.
When should I choose Buildroot over Yocto?
Buildroot shines for small, single-purpose systems with straightforward dependency graphs and image-based updates.
Yocto is stronger when you need layered BSPs, multiple products from one codebase, or long-term maintenance at scale.
9) Key Takeaways
- Start with constraints: hardware, footprint, security, and update policy guide the choice more than brand names.
- Prototype fast, converge deliberately: use Debian/Ubuntu for discovery; migrate to Yocto/Buildroot for production control.
- Automate everything: reproducible builds, CI, signed artifacts, and hardware-in-the-loop OTA tests prevent “it works on my machine.”
- Design for maintenance: choose LTS kernels, track CVEs, and document your BSP and device tree changes.
With a methodical evaluation and a strong build/update pipeline, Embedded Linux can deliver the performance, security,
and longevity modern products demand.